Australia
Preventing a data breach isn't about finding a single magic bullet. It’s a multi-layered strategy that weaves together proactive human diligence, robust tech controls, and constant monitoring. Think of it as creating a defence system where employee awareness, strict access rules, and up-to-date software work in concert to protect your most valuable asset: your information.
The Evolving Threat of Data Breaches in Australia
The conversation around data security has shifted dramatically. It’s no longer a hypothetical risk talked about in boardrooms but a tangible, daily threat hitting Australian businesses hard. The reality is that attackers are using increasingly sophisticated methods to target organisations of all sizes, making the threat landscape more complex than ever.
This isn’t just an IT department problem. A breach hits every part of a business, from customer trust to financial stability. Small businesses, in particular, often fall into the trap of thinking they’re too small to be a target. In reality, their potentially less fortified defences make them an attractive and easy entry point for criminals. To build a solid defence, you first have to understand the specific threats you’re up against right now.
Understanding the Current Threat Landscape
Recent trends show a clear and worrying escalation in both how often cyber incidents are happening and how severe they are. For instance, Australia saw a 25% year-on-year increase in reported data breaches, with businesses and government agencies lodging a record 1,113 notifications with the Office of the Australian Information Commissioner (OAIC).
What’s really telling is that a staggering 69% of these breaches were the result of malicious or criminal attacks. These aren’t accidental leaks; they are deliberate, targeted assaults on business data. You can dig deeper into these trends on the OAIC website.
This screenshot from the OAIC's official website highlights the agency's central role in managing data breach notifications and providing crucial guidance to businesses.

The data makes one thing crystal clear: sectors like healthcare and finance remain prime targets. Why? Because of the high-value, sensitive personal and financial information they handle.
Here’s a snapshot of what the current environment looks like.
Australia's Key Data Breach Statistics
Recent reports paint a stark picture of the threats Australian businesses are facing. Understanding these numbers is the first step toward building a more resilient defence.
| Statistic | Finding | Implication for Businesses |
|---|---|---|
| 1,113 Breaches Reported | A record number of notifications were made to the OAIC in the last reporting period. | The likelihood of experiencing a breach is higher than ever; it's a matter of "when," not "if." |
| 69% from Criminal Attacks | The vast majority of breaches are deliberate acts, including ransomware, phishing, and hacking. | Your defence strategy must focus on actively countering malicious attackers, not just preventing accidents. |
| 25% Year-on-Year Increase | The frequency of reported breaches is growing rapidly, indicating an escalating threat level. | Security can't be a one-off project. It requires continuous investment and adaptation. |
| Top Targeted Sectors | Healthcare and finance consistently report the highest number of breaches. | If you hold sensitive data (PII, financial records), you are a high-value target and need extra layers of security. |
These statistics aren't just numbers on a page; they represent real businesses facing serious disruption. The threat is active, organised, and growing more sophisticated every day.
The Real-World Impact on Businesses
The fallout from a data breach extends far beyond the immediate financial hit. The true cost is a painful mix of damaging factors that can cripple an organisation long-term.
- Reputational Damage: Customer trust is hard to win and incredibly easy to lose. A publicised breach can shatter confidence in your brand, sending clients straight to your competitors.
- Financial Costs: This is a long list. It includes regulatory fines, legal fees, the expense of notifying customers, providing credit monitoring services, and the cost of PR efforts to try and repair your brand's image.
- Operational Disruption: Simply recovering from a breach can bring your business to a grinding halt for days or even weeks. That means lost revenue and a massive drop in productivity.
A strong security posture is no longer a "best practice." It is a fundamental business necessity for survival and for maintaining the trust you've worked so hard to build. Ignoring this is a gamble most businesses simply can't afford to take.
For smaller organisations, building this defence can feel overwhelming, but it all starts with getting the fundamentals right. You can explore our guide on cybersecurity for small businesses to learn about essential protective measures tailored to your needs.
The key takeaway is simple but critical: prevention is always, always more cost-effective than recovery.
Building a Human-Centric Security Culture
Technology is a powerful shield, but it can't prevent data breaches alone. The most persistent and often overlooked vulnerability in any organisation is its people. Creating a genuine, human-centric security culture is about moving beyond once-a-year training and empowering your team to become your most effective defence.
This means shifting the mindset from security as a restrictive set of rules to a shared responsibility. When employees understand the why behind security policies, they are far more likely to become active participants in protecting the organisation's data. It’s about building a team of security advocates, not just compliant staff.
Moving Beyond Checkbox Training
Let's be honest, traditional security training often fails. It's boring, infrequent, and completely disconnected from the reality of a busy workday. A yearly slideshow on password policies does little to prepare someone for a sophisticated, personalised phishing email that lands in their inbox on a Tuesday morning.
Effective training needs to be continuous, engaging, and relevant. The goal isn't just to teach rules but to build critical thinking skills.
- Scenario-Based Learning: Instead of just listing threats, create realistic simulations. Walk employees through a Business Email Compromise (BEC) scenario where an attacker impersonates the CEO requesting an urgent fund transfer.
- Regular Phishing Simulations: Conduct frequent, unannounced phishing tests. These exercises provide a safe environment for your team to make mistakes and learn from them without real-world consequences.
- Micro-Learning Modules: Deliver short, focused training snippets throughout the year. A five-minute video on identifying malicious links is far more digestible and memorable than a two-hour annual seminar.
This approach transforms training from a passive event into an active, ongoing process that reinforces secure habits.

The most effective security culture is one where employees feel comfortable reporting suspicious activity without fear of blame. Fostering this psychological safety turns every team member into a potential sensor for your security team.
Empowering Employees as Active Defenders
Empowerment comes from giving your team the right knowledge and tools. It's about showing them exactly what to look for and making it dead simple for them to report potential threats. This proactive stance is essential for shutting down data breaches before they escalate.
A crucial part of this is understanding the human element that attackers exploit. In Australia, Business Email Compromise (BEC) was the top reported cyber incident type, and attackers are becoming alarmingly good at bypassing technical controls. In a staggering 75% of analysed BEC cases, attackers managed to get past multi-factor authentication, highlighting that technology isn't foolproof.
The human factor remains the weakest link; a recent survey found nearly two-thirds of regional IT leaders admitted to clicking malicious links themselves. You can dive deeper into these cyber threats in the latest threat report from CyberCX.
This is where understanding modern authentication methods becomes vital. While MFA is critical, not all forms are created equal. You can get a clearer picture by reading our guide on what is two-factor authentication and how it works to protect accounts.
Developing Supportive and Clear Policies
Your security policies should act as guardrails, not roadblocks. If policies are overly complex or get in the way of productivity, employees will inevitably find workarounds—often creating new security holes in the process.
Effective policies are clear, concise, and designed to support your team, not fight them.
- Acceptable Use Policy (AUP): Clearly define what’s considered appropriate use of company systems and data. This should cover guidelines on using personal devices, accessing public Wi-Fi, and handling sensitive information.
- Password Management: Go beyond just requiring complex passwords. Implement policies that mandate the use of a password manager and enable multi-factor authentication across all critical services.
- Data Handling Procedures: Provide straightforward instructions for classifying, storing, and sharing sensitive data. For example, specify that client financial records must only be stored in an encrypted, access-controlled folder and never shared via email.
- Incident Reporting: Create a simple, blame-free process for reporting suspected security incidents. An employee who clicks a suspicious link should know exactly who to contact immediately without fear of punishment.
By weaving together engaging training, genuine empowerment, and supportive policies, you build a resilient security culture. This "human firewall" becomes one of your most valuable assets in the ongoing fight to prevent data breaches.
Implementing Essential Technical Controls
Training your people is the first line of defence, but the next critical layer is putting robust technical safeguards in place. Think of these controls as the digital locks, alarms, and reinforced walls that protect your data from the inside out. They’re designed to shrink your attack surface and contain any threats that manage to slip past your human firewall.
This is where we move from theory into practical, hands-on security. When configured correctly, technology acts as a powerful force multiplier, automating protection and enforcing the security policies you’ve already established. It’s not about buying every shiny new tool, but strategically deploying foundational controls that deliver the biggest impact.

Fortifying Access with Advanced Authentication
Multi-Factor Authentication (MFA) is completely non-negotiable. It’s one of the single most effective controls you can enable to stop unauthorised access, which is the end goal of most cyber attacks. But just turning it on isn't enough anymore.
Attackers have become adept at bypassing basic MFA, often through "MFA fatigue" attacks where they spam a user with push notifications until one is accidentally approved. To counter this, your MFA implementation needs to be smarter.
- Use Phishing-Resistant Methods: Move away from SMS codes and simple push notifications. Instead, prioritise methods like FIDO2 security keys or authenticator apps that require number matching to approve a login.
- Configure Conditional Access: Set up policies that scrutinise login attempts. For example, you can automatically block logins from unfamiliar locations or demand a higher level of authentication if a user tries to access a highly sensitive system.
This approach elevates MFA from a simple checkbox to a dynamic, context-aware defence that significantly raises the bar for attackers.
Embracing the Principle of Least Privilege
The Principle of Least Privilege (PoLP) is a foundational security concept: a user should only have the absolute minimum level of access—or permissions—needed to do their job. This simple idea drastically limits the potential damage if an account is ever compromised.
If a marketing employee's account is breached, the attacker shouldn't be able to wander into financial records or core IT infrastructure. Implementing PoLP involves a few key actions.
Think of it like giving out keys. You wouldn't give every employee a master key to the entire building. Instead, you give the receptionist a key to the front door and the finance manager a key to the accounts office—nothing more.
This same logic has to be applied to your digital assets. Segment your network and restrict user permissions to match their roles. For instance, creating separate network zones for your public-facing web servers and your internal databases prevents an attacker who compromises one from easily moving to the other. Regular access reviews are also critical to ensure permissions don't pile up over time, a problem known as "privilege creep."
Securing Your Endpoints and Encrypting Data
Every device that connects to your network—laptops, servers, mobile phones—is an endpoint. And each one represents a potential entry point for an attack. Modern security has moved far beyond traditional antivirus software.
You need robust Endpoint Detection and Response (EDR) solutions. These tools actively monitor endpoint activity for suspicious behaviour, allowing you to detect and shut down threats in real-time before a full-blown breach can happen. For a deeper understanding of this technology, you can learn more about what is endpoint protection and how it secures your devices.
Alongside endpoint security, data encryption is essential. Encryption scrambles your data, making it unreadable to anyone without the correct decryption key. This protection must be applied in two states:
- Data at Rest: This is data stored on hard drives, servers, or in the cloud. Encrypting this means that even if an attacker steals a physical device, the information on it is useless.
- Data in Transit: This refers to data moving across your network or the internet. Using technologies like TLS ensures that information sent between a user and a web server, for instance, cannot be intercepted and read.
This two-pronged strategy ensures your data is protected whether it's sitting still or on the move. And when it's time to retire old hardware, proper data destruction is a critical final step. It's crucial to understand how to securely wipe a hard drive to ensure data is irrecoverably erased.
Maintaining a Rigorous Patching Schedule
Finally, one of the most common—and easily avoidable—ways attackers gain entry is by exploiting known vulnerabilities in outdated software. When a software vendor releases a security patch, they are essentially publicising a weakness.
Delaying these patches gives attackers a clear window of opportunity. A timely, organised patching schedule is one of the cornerstones of good security hygiene. Automate updates where you can and have a clear process for testing and deploying critical patches as soon as they become available. This simple discipline closes the doors that cyber criminals are actively looking for every single day.
Shifting to a Proactive Monitoring Strategy
A strong defence isn't just about building high walls; it's about being able to spot threats in real-time. The biggest shift you can make in preventing data breaches is moving from a passive, "set and forget" mindset to an active security posture. This means you're actively looking for trouble instead of just waiting for an alarm to go off.
Think of proactive monitoring as creating a live, dynamic view of your entire network. It gives your security team the power to see unusual activity, flag potential intrusions, and shut them down before they escalate into a full-blown crisis. Without this visibility, you’re flying blind.
Embracing Continuous Network Visibility
To properly watch over your digital environment, you need the right tools to collect and make sense of security data. It’s simply impossible for a human to watch every single connection and log entry in real-time. This is where specialised systems come in, acting as your digital watchdogs.
Two key technologies form the foundation of a solid monitoring strategy:
- Intrusion Detection Systems (IDS): Think of an IDS as a burglar alarm for your network. It scans traffic for known malicious patterns or suspicious activity that deviates from the norm. When it spots a potential threat, it fires off an alert to your team for investigation.
- Security Information and Event Management (SIEM): A SIEM is your central command centre. It pulls log data from everywhere—firewalls, servers, endpoints, applications—and pieces it all together to find patterns an IDS might miss. For instance, it could connect a failed login attempt on a server with a strange email attachment opened by a user just minutes earlier.
Using these tools, you can turn mountains of raw data into actionable security intelligence. This helps your team focus on genuine threats instead of getting lost in the noise of everyday network chatter.
A proactive monitoring strategy doesn't just catch attackers; it creates an environment where they know they're being watched. This alone can be a powerful deterrent, encouraging them to move on to an easier, less-observed target.
From Defence to Offence with Vulnerability Assessments
While real-time monitoring keeps an eye on incoming attacks, you also need to actively hunt for weaknesses in your own defences. This is where vulnerability scanning and penetration testing come into play. It’s about putting on an attacker’s hat and trying to break into your own systems before someone with malicious intent does.
This proactive approach helps you find and patch security gaps that might otherwise go unnoticed for months. You get to see your organisation from an adversary's perspective, which is an invaluable part of learning how to prevent data breaches.
Regular Scans and Penetration Tests
Think of vulnerability scans and penetration tests as two different but complementary types of health checks for your security.
Vulnerability scanning is like an automated diagnostic tool. It regularly sweeps your networks, systems, and applications for known issues, such as unpatched software or weak configurations. The result is usually a report that prioritises weaknesses by severity, giving your IT team a clear to-do list for patching.
Penetration testing (or pen testing) is a much more hands-on, manual process. You hire ethical hackers to simulate a real-world attack on your organisation. They’ll actively try to exploit vulnerabilities to see how far they can get, whether that’s accessing sensitive data or taking control of critical systems.
A pen test provides a true measure of your security's effectiveness under pressure. For example, a test might reveal that while your technical controls are strong, a clever phishing email could still trick an employee into giving up credentials, allowing an "attacker" to bypass your defences. These insights are crucial for refining both your technical and human security layers.
The operating system you use also plays a role in your overall security posture. For businesses evaluating their options, understanding the security features built into different versions is important. You can find useful comparisons in our guide on the difference between Windows 11 Home and Pro, which covers features relevant to securing business environments.
Developing a Resilient Incident Response Plan
Let's be realistic. Even with the best preventative controls, you have to be prepared for the worst-case scenario. When a data breach is happening in real time, the last thing you want is your team trying to figure out what to do next. The chaos and pressure of an attack can lead to costly mistakes, which is why a well-rehearsed incident response plan is absolutely essential. It's what keeps a bad situation from spiralling into a complete disaster.
A solid plan is more than a document; it's a detailed roadmap that guides your team from the first sign of trouble all the way through to recovery. It takes the guesswork out of the equation, clarifies who does what, and ensures everyone acts in a coordinated, efficient way. The whole point is to minimise damage, get back to business faster, and protect your company’s reputation.
This process flow gives a clear picture of the core stages involved, from detection right through to the final analysis.
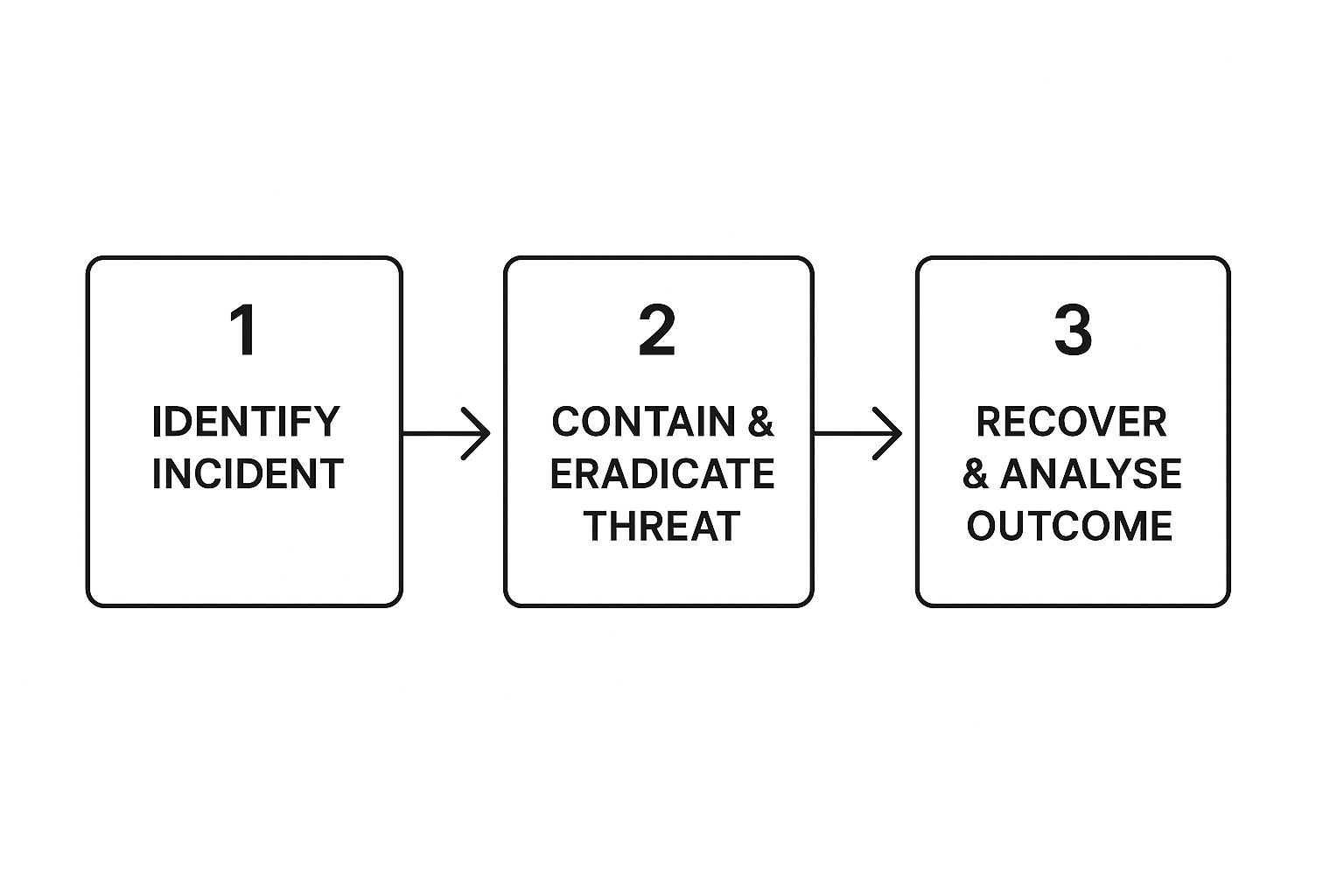
Having this kind of sequential path ensures no critical steps are missed when tensions are running high during a security incident.
Assembling Your Core Response Team
Before a crisis hits, you need to know exactly who is on your Incident Response Team (IRT). This isn't just a job for the IT department; it needs to be a cross-functional group with crystal-clear roles, ready to jump into action at a moment's notice.
Your IRT should pull in people from several key areas:
- IT and Security: These are your technical experts. They’re responsible for finding, containing, and getting the threat out of your systems.
- Executive Leadership: You need someone with the authority to make critical business decisions, sign off on resources, and steer the overall strategy.
- Legal Counsel: A data breach comes with complex legal duties. Your legal expert will navigate these, especially reporting requirements under Australia’s Notifiable Data Breaches (NDB) scheme.
- Communications/PR: This team manages the message. They handle all internal and external communications to ensure employees, customers, and regulators get clear, consistent information.
- Human Resources: HR steps in to manage any employee-related issues, like compromised staff accounts or internal policy violations that may have contributed to the breach.
It's crucial to have this team defined well in advance, complete with designated backups for every role. Make sure their contact information is stored securely and is accessible even if your primary communication systems go down.
A classic mistake is keeping your incident response plan only on the company network. If that network gets locked down by ransomware, your plan is completely useless. Always keep secure, offline copies where key team members can get to them.
Outlining the Phases of Response
A truly effective plan is broken down into distinct phases. This structure creates a logical flow from detection to recovery, with each stage having specific goals and actions that need to be ticked off before you can move on.
The table below breaks down the six key phases of an effective incident response plan, outlining the primary goal and key actions for each.
| Phase | Primary Goal | Key Actions |
|---|---|---|
| Preparation | To build and maintain a state of readiness. | Assembling the IRT, acquiring tools, conducting training and drills. |
| Identification | To verify an incident and assess its scope and impact. | Analysing alerts, confirming the breach, determining systems affected. |
| Containment | To stop the incident from spreading and causing more damage. | Isolating networks, blocking malicious IPs, disabling compromised accounts. |
| Eradication | To completely remove the threat from the environment. | Eliminating malware, patching vulnerabilities, removing unauthorised access. |
| Recovery | To restore systems to normal, secure operation. | Restoring from clean backups, monitoring systems, verifying functionality. |
| Post-Incident Analysis | To learn from the incident and improve future defences. | Conducting a root cause analysis, documenting lessons learned, updating the plan. |
By breaking the process down into these manageable stages, you create a repeatable and effective framework for handling any security incident. Regular drills and tabletop exercises are essential to ensure everyone knows their role and can execute the plan under pressure.
1. Preparation
This is the ongoing work you do to stay ready. It’s where you build your plan, assemble your IRT, get the right tools (like forensic software), and run regular training exercises.
2. Identification
This kicks off the moment an alert is triggered. The goal here is simple: confirm if an incident has actually happened, figure out how big it is, and understand the potential damage.
3. Containment
Once you've confirmed a breach, the immediate priority is to stop it from spreading. This might mean pulling affected systems off the network, blocking malicious IP addresses, or shutting down certain services temporarily.
4. Eradication
With the threat contained, you can now focus on removing it completely. This involves getting rid of malware, disabling breached user accounts, and patching the vulnerabilities that the attackers exploited in the first place.
5. Recovery
Now that the threat is gone, it’s time to get back to business. This means carefully bringing systems back online from clean backups and monitoring everything closely to make sure there are no signs of reinfection. When it comes to OS recovery, understanding different versions is vital. For more on stable, secure options, you can read our article on the benefits of Windows 11 LTSC.
6. Post-Incident Analysis
This might be the most important phase for your long-term security. Your team needs to do a full review of the incident. Document what happened, what went well, and what didn’t. The lessons you learn here are fed straight back into your preparation phase, making your defences stronger for next time.
Common Questions About Data Breach Prevention
Even with a solid strategy on paper, practical questions always pop up when you start putting it all into action. Let’s tackle some of the most common queries I hear from Australian business owners and IT managers, with clear, no-nonsense answers to help you sharpen your defences.
How Often Should We Be Doing Security Training?
If you’re still thinking of security training as a once-a-year, tick-a-box exercise, it’s time for a rethink. That model is broken. Modern threats move way too fast for annual training to be effective; the information is often outdated within months, and staff forget it just as quickly.
Real security awareness needs to be a constant, low-level hum in the background of your business. I recommend a layered approach. Run focused training sessions each quarter, zeroing in on a specific, relevant threat like Business Email Compromise (BEC) or the latest ransomware tactics. Then, back this up with monthly simulated phishing campaigns. This keeps your team’s reflexes sharp and ensures security stays top-of-mind, turning it from a yearly chore into an everyday habit.
Is My Small Business Really a Target?
Yes, without a doubt. Believing your business is "too small to be a target" is one of the most dangerous assumptions you can make. Cybercriminals are opportunistic; they often see smaller businesses as the perfect target precisely because they assume they have weaker security and fewer resources to fight back.
It gets worse. Attackers are smart, and they often use smaller businesses as a backdoor to a bigger prize. They might breach your systems to launch a supply chain attack against one of your larger, more valuable partners. The hard truth is that every business that holds valuable data is a potential target, regardless of size.
Thinking your business is too small to attract cybercriminals is like leaving your car unlocked in a quiet street because you don't think it's fancy enough to be stolen. Unfortunately, opportunistic thieves look for the easiest entry point, not the most valuable prize.
What Is the Single Most Important First Step?
If you can only do one thing right now, make it this: implement mandatory, properly configured Multi-Factor Authentication (MFA) on every critical system. This isn't negotiable. It needs to be on your email, your VPN, all your cloud services, and especially any accounts with administrative privileges.
No single defence is a silver bullet, but strong MFA is the closest thing we have to shutting down the most common attack vector: stolen login details. Whenever you can, opt for phishing-resistant MFA methods like FIDO2 security keys or number-matching authenticator apps. They’re a significant step up in security from the older, less secure SMS codes.
Does Cyber Insurance Mean I Don't Need Strong Security?
Absolutely not. That’s like thinking a good health insurance policy means you can stop eating well and exercising. Cyber insurance is a crucial financial safety net, not a replacement for good security hygiene. It’s there to help you manage the chaotic aftermath of a breach, covering costs like legal fees, customer notifications, and regulatory fines.
But here’s the thing: insurers aren't writing blank cheques anymore. To even get a policy, you’ll have to prove you have a strong security posture in the first place. They’ll want to see evidence of essential controls like MFA, a regular software patching schedule, and consistent employee training. Strong security reduces the chances of a breach happening; insurance is there to help manage the financial fallout if it still does.
At Digital Hub Key, we provide genuine, affordable software licences to help you build a secure and efficient IT foundation. Secure your systems with authentic Windows and Antivirus keys today by visiting us at https://digitalhubkey.com.






[…] As you can see, we place a heavy emphasis on performance (40%), because security software that slows your device to a crawl isn't a solution—it's just another problem. This structured approach lets you see exactly how each product stacks up, giving you the power to make a decision based on clear, data-driven insights. Grasping these fundamentals is also a core part of learning how to prevent data breaches. […]
[…] Advanced Ransomware: This nasty malware encrypts your personal files and demands money to get them back. Dedicated ransomware protection creates secure folders for your critical data, stopping unauthorised programs from messing with them. You can find more strategies in our guide on how to prevent data breaches. […]
[…] crucial part of keeping your digital assets clean and secure involves knowing how to prevent data breaches and protecting your sensitive information. Regular maintenance not only keeps things tidy but also […]