Australia
Think of your business network as a fortress. In the old days, you could protect it with a strong wall and a single gatekeeper—your firewall. But today, the fortress has countless doors and windows. Every laptop, server, smartphone, and tablet is a potential entry point for an attacker.
This is where endpoint protection comes in. It’s the modern-day security strategy designed to guard every single one of those entry points, no matter where they are.
Your Digital Frontline: What Is Endpoint Protection?

Endpoint protection is a centralised approach to securing every device that connects to your corporate network, whether it’s sitting in your main office or on an employee’s kitchen table hundreds of kilometres away.
The old security perimeter has completely dissolved. With the massive shift to remote work and the rise of "Bring Your Own Device" (BYOD) policies, your company's attack surface has exploded. Every device is now on the frontline, exposed to potential threats.
This new reality makes traditional antivirus software feel like a relic. Antivirus was great at spotting well-known, documented threats, but it’s completely outmatched by the sophisticated, never-before-seen malware that cybercriminals cook up every single day. Today's threats are smarter, so your defences have to be, too.
To give you a clearer picture, here’s a quick breakdown of what endpoint protection is all about.
Endpoint Protection At a Glance
| Core Concept | Primary Goal | Devices Protected |
|---|---|---|
| Centralised Security | To detect, prevent, and respond to threats on all network-connected devices from a single point of control. | Laptops, desktops, servers, smartphones, tablets, and IoT devices. |
| Proactive Defence | To stop attacks before they cause damage, rather than just cleaning up after an infection. | Any device that can access corporate data or network resources. |
| Complete Visibility | To provide security teams with a clear view of all endpoint activity to identify and investigate suspicious behaviour. | Both company-owned and personal devices (BYOD) used for work. |
Ultimately, it’s about creating a unified, intelligent defence that can keep up with the complexity of modern business.
The Evolution of Endpoint Defence
Modern endpoint protection platforms have evolved far beyond simple virus scanning. They are now multi-layered defence systems, often managed from a single cloud-based console. This gives security teams total visibility and control, ensuring consistent security rules are enforced everywhere, automatically.
These contemporary platforms are packed with advanced tools:
- Next-Generation Antivirus (NGAV): This isn't your old antivirus. It uses artificial intelligence and behavioural analysis to spot and block brand-new threats it has never encountered before.
- Device Control: This feature lets you manage which peripheral devices, like USB drives, can connect to your endpoints. It's a simple but powerful way to stop data theft or malware infections from physical devices.
- Application Whitelisting: This flips security on its head. Instead of trying to block millions of bad programs, it only allows pre-approved, trusted software to run, effectively shutting the door on anything unauthorised or malicious.
Endpoint protection is no longer just about preventing infection; it’s about creating resilience. It operates on the assumption that a breach is always possible and gives you the tools to detect, investigate, and respond in moments to minimise the damage.
This evolution is non-negotiable. A core part of this defence is ensuring every device runs a secure, up-to-date operating system. For more on this foundational step, you can explore our guide on how to safely purchase a Windows 10 key to keep your systems fully supported.
When you pair a secure OS with a powerful endpoint solution, you build a truly formidable defence against modern cyber threats.
The Core Components of Modern Endpoint Security

A modern Endpoint Protection Platform (EPP) is a world away from the simple antivirus programs of the past. Think of it as a multi-layered shield, where several advanced technologies work in concert to build a truly robust defence.
Getting to grips with these core components is the key to understanding what real endpoint protection offers. Each layer has a distinct job, from proactively stopping brand-new threats to giving your security team deep investigative powers. Together, they create a defence that’s tough enough for today's complex cyber threats.
Next-Generation Antivirus (NGAV)
The first and most proactive layer of defence is Next-Generation Antivirus (NGAV). Old-school antivirus relied on a library of known virus "signatures" to spot threats. NGAV is much smarter. It uses artificial intelligence (AI) and machine learning to analyse how a file behaves.
This allows it to spot and shut down malicious code it’s never encountered before, including zero-day exploits and other sophisticated malware. Imagine a security guard who can spot a burglar not just by recognising their face, but by the suspicious way they’re rattling door handles. That’s NGAV in action—it focuses on malicious intent, not just known identities.
This forward-looking approach is critical for stopping new threats cold. But while NGAV is vital, it's just one piece of the puzzle. It's often paired with other layers for deeper security, such as requiring strong user verification. You can learn more about how to strengthen access security in our guide on what is two-factor authentication.
Endpoint Detection and Response (EDR)
So, what happens when a particularly advanced threat slips past those initial defences? This is where Endpoint Detection and Response (EDR) comes in. Think of EDR as a black box flight recorder for your devices. It’s always on, continuously monitoring and logging every single activity—from a new process starting to a network connection being made.
This incredibly detailed log gives security teams the deep visibility they need to investigate an incident properly. When a breach is suspected, EDR tools allow analysts to:
- Hunt for Threats: Actively search for signs of a compromise across every endpoint in the network.
- Investigate Alerts: Unravel the entire story of an attack, tracing it back to its origin to understand the full impact.
- Respond and Remediate: Quickly isolate infected devices from the network and stamp out the threat before it can spread.
EDR works from a philosophy of "assume breach." It acknowledges that no prevention is foolproof and provides the tools you need for rapid detection and clean-up when an attacker inevitably gets through.
Device and Application Control
Modern EPPs go beyond just fighting malware; they also give you control over how devices and applications are actually used. These features are all about shrinking your attack surface by closing off common entry points for threats.
Device Control lets you manage peripheral hardware like USB sticks and external hard drives—notorious vectors for malware. You can set policies to block all USB devices outright or, more practically, only allow company-approved, encrypted ones.
Application Control, sometimes called whitelisting, takes security a step further. Instead of trying to maintain a massive blacklist of millions of malicious programs, you simply create a pre-approved "whitelist" of safe software. If it’s not on the list, it doesn’t run. Period.
This proactive stance is incredibly effective at blocking any unauthorised or malicious programs from ever executing. Businesses are clearly taking notice, as the endpoint security market in Australia & Oceania is projected to hit US$453.78 million by 2025, fuelled by digital transformation and the need for stronger defences. For a deeper analysis of these regional trends, you can explore the full market projection on Statista.
Why Endpoint Protection Is No Longer Optional
Not so long ago, securing a business was like defending a castle. You had a moat, high walls, and one heavily guarded gate—the network perimeter. Today, that castle has been replaced by an open-plan office with hundreds of doors left wide open.
The old perimeter has all but vanished, thanks to remote work and the now-common ‘Bring Your Own Device’ (BYOD) policies. This shift means every employee's home network, the local cafe's Wi-Fi, and their personal smartphone is now a potential entry point into your corporate environment. Cybercriminals know this, and they’ve designed modern threats like ransomware and fileless malware specifically to exploit these unguarded endpoints.
An unprotected laptop or mobile device isn't just a personal risk anymore; it's a direct threat to your entire organisation.
The New Reality of Business Security
The modern work environment has permanently stretched the corporate attack surface. A threat that slips through one remote employee's laptop can spread like wildfire across the entire network, leading to devastating data breaches, operational shutdowns, and severe financial losses. To really get why endpoint protection is non-negotiable, you have to see its role in the bigger picture of cybersecurity.
Endpoint protection isn't an IT expense to be minimised; it's a fundamental investment in business continuity. It ensures that your first line of defence—your devices—is strong enough to withstand the constant pressure of today’s advanced threats.
This reality is especially stark in Australia, where cyber threats have escalated dramatically. Global analyses show that over 70% of organisations in the Asia-Pacific region, including Australia, were hit by a cyberattack in 2022. This surge is directly tied to the explosion of smart devices, which have created countless new ways for attackers to get in. You can discover more about these regional security trends on Marketdata Forecast.
Guarding Against Financially Motivated Attacks
Let's be clear: today's cyberattacks are a business. They are designed for one thing—maximum financial gain. Attackers go after endpoints because they are, all too often, the weakest link in the security chain.
Here are a few of the common threats designed to exploit them:
- Ransomware: This malware is a digital hostage situation. It encrypts critical files on a device and demands a hefty ransom for their release. A single infected endpoint can quickly lock down an entire network's data.
- Fileless Malware: This is the ghost in the machine. This sneaky attack operates directly in a computer's memory (RAM), leaving no files on the hard drive for traditional antivirus software to find. Only advanced endpoint tools can spot it.
- Phishing Attacks: These are fraudulent emails that trick employees into giving up their login details or downloading malware. A solid endpoint solution can block malicious links and attachments before an employee even gets the chance to click.
Ultimately, leaving your endpoints unsecured is like leaving your doors unlocked in a high-crime neighbourhood. It’s not a matter of if a breach will happen, but when. Putting a comprehensive endpoint protection strategy in place is the most important step you can take to secure your operations, protect your data, and keep your business resilient.
Comparing Endpoint Protection Deployment Models
Picking the right endpoint protection solution goes way beyond just comparing feature lists. You also need to think about how it’s going to fit into your organisation. The way a platform is deployed dictates who’s responsible for managing it, where your security data is stored, and how easily it can scale as your business grows.
Getting your head around the different deployment models is the key to finding a solution that actually works for your security needs, not against them. The three main flavours are on-premises, cloud-managed, and hybrid, each offering a different mix of control, cost, and effort.
The On-Premises Model: Full Control
The on-premises approach is the old-school way of doing things, where you host and manage everything yourself. You buy the software licences, set up the management server on your own hardware in your own data centre, and your IT team handles every single update, patch, and hiccup.
This model gives you the ultimate level of control over your security infrastructure and data, which is a big deal for some organisations. But that control comes with a hefty price tag. It demands a big upfront investment in server hardware and a skilled IT team with the time to babysit it. Scaling up is also a slow, expensive process—it means buying and configuring more physical boxes.
The Cloud-Managed Model: Flexible and Scalable
On the flip side, a cloud-managed model is delivered as a Software-as-a-Service (SaaS) solution. The vendor takes care of hosting and maintaining the entire management infrastructure in the cloud. All your team has to do is roll out lightweight agents to your endpoints and manage everything from a simple web browser.
This approach brings incredible flexibility and scalability, making it a perfect fit for businesses with remote teams or a lean IT department. There’s zero server hardware to buy or maintain, and the vendor handles all the security updates automatically. This means you’re always protected against the latest threats without lifting a finger.
The core trade-off is simple: on-premises offers granular control at the cost of high resource requirements, while cloud-managed delivers simplicity and scalability by entrusting management to the vendor.
This infographic paints a clear picture of how these models stack up against each other based on control, resource needs, and scalability.
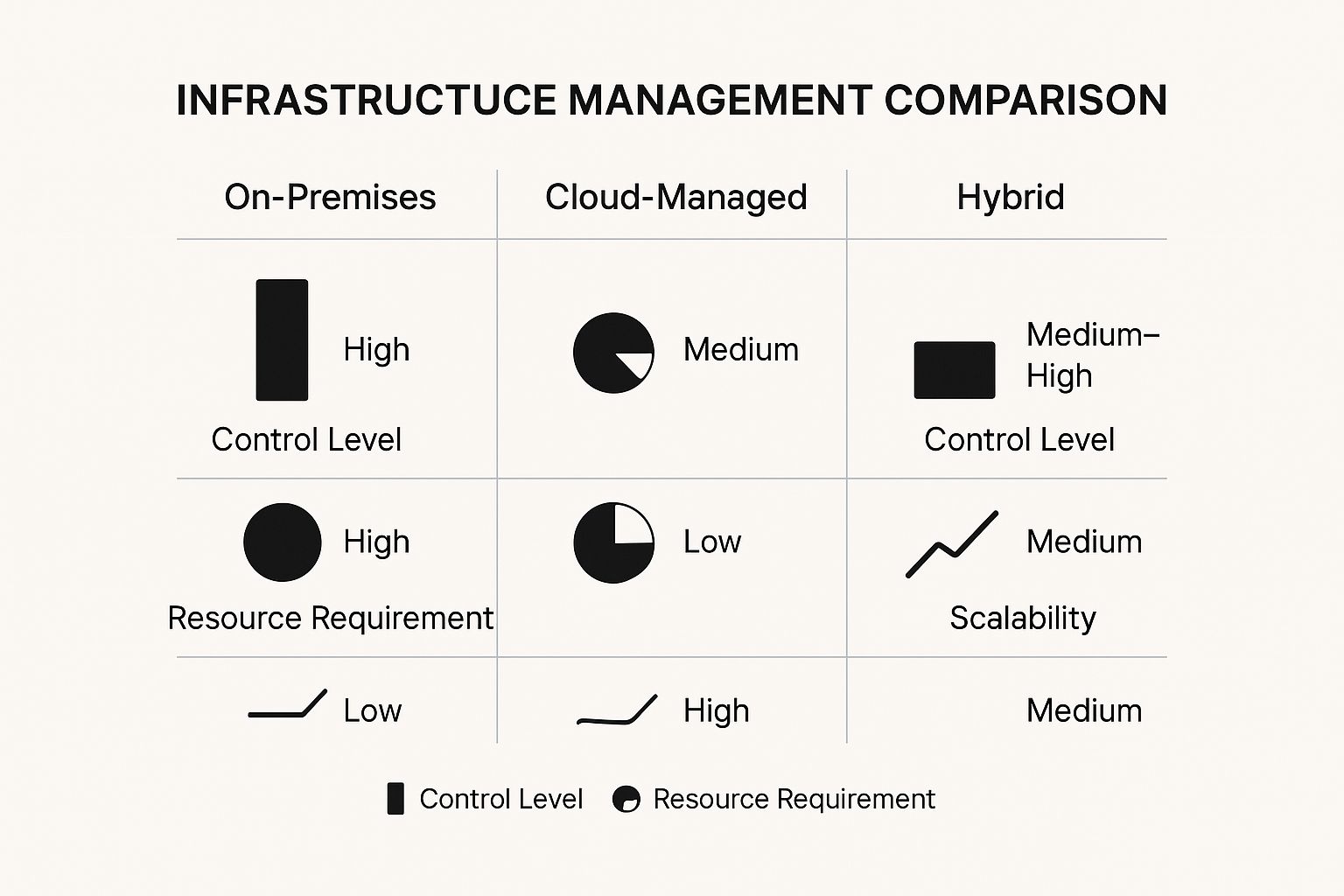
As you can see, cloud-based solutions dramatically lower the resource burden while maximising scalability—a critical advantage for any modern, distributed workforce.
For a clearer, side-by-side view, let's break down the key differences between the two main models.
On-Premises vs Cloud-Managed Endpoint Protection
This table offers a comparative look at the two primary deployment models for endpoint protection, helping you decide which is the right fit for your business.
| Feature | On-Premises Solution | Cloud-Managed Solution |
|---|---|---|
| Initial Cost | High (requires hardware, software licences) | Low (subscription-based, no hardware needed) |
| Maintenance | Managed entirely by your in-house IT team | Managed by the vendor; updates are automatic |
| Control | Complete control over data and infrastructure | Less direct control; you trust the vendor |
| Scalability | Slow and expensive; requires new hardware | Fast and easy; scales on demand with a click |
| Accessibility | Limited to your internal network (VPN needed) | Accessible from anywhere with an internet connection |
| IT Resources | Requires a dedicated, skilled IT team | Minimal IT overhead required |
Ultimately, the choice depends on your organisation's priorities. If total control and data residency are non-negotiable, on-premises might be the only way. But for most businesses prioritising agility, scalability, and efficiency, the cloud is the clear winner.
The Hybrid Model: Best of Both Worlds
A hybrid model tries to give you the best of both worlds by blending the on-prem and cloud approaches. A common setup involves a central cloud management console that talks to on-premises components, like a local data repository or management server.
This is a great option for organisations that need the ease of cloud management but have to keep sensitive security data on-site for strict compliance or regulatory reasons. For some businesses, especially those in regulated fields, maintaining absolute control over certain systems is a must. This can also include running specific, long-term supported operating systems. You can learn more about managing these environments with our guide on Windows 11 LTSC.
Choosing the right deployment model ensures your endpoint security strategy is a perfect match for both your day-to-day operations and your long-term compliance goals.
The Role of AI in Proactive Endpoint Defense
Traditional security was always a step behind. It was reactive, like a security guard responding to an alarm after it's already been tripped. Modern endpoint protection, driven by Artificial Intelligence (AI), flips that script entirely. It's more like having a security expert who predicts where a burglar might try to break in and reinforces that spot before they even get close.
This forward-thinking defence isn't just a nice-to-have; it's essential. The progress in artificial intelligence is completely reshaping endpoint security, enabling a far more proactive approach to threat detection. It's also helping organisations meet rigorous benchmarks, like understanding AI-powered risk detection within global information security standards like ISO 27001.
By crunching immense datasets from millions of devices, AI and Machine Learning (ML) algorithms learn what normal, everyday activity looks like. This baseline allows them to spot the tiniest deviations that signal an attack is underway—even from brand-new malware that’s never been seen before.
From Signatures to Behaviour
Old-school antivirus software was basically a bouncer with a list. If a file’s signature was on the blacklist, it was blocked. If not, it was let in. AI-driven endpoint protection takes a much smarter approach by focusing on actions, not just identities. This is called behavioural analysis.
Instead of asking, "Is this file on my list of known threats?" it asks, "Is this program acting suspiciously?"
For example, an AI can instantly detect and block a process that suddenly tries to:
- Encrypt huge numbers of files—a classic calling card of ransomware.
- Poke around in sensitive system memory where user credentials are kept.
- Talk to a known malicious command-and-control server on the internet.
This method allows modern endpoint solutions to shut down zero-day exploits and fileless malware, the kind of advanced threats designed to be completely invisible to older, signature-based tools.
AI doesn't just build a better mousetrap; it redesigns the entire security model. It shifts the focus from recognising past threats to predicting and preventing future ones, making your endpoint defence far more resilient.
The Power of Predictive Threat Modelling
Beyond watching what's happening right now, AI is brilliant at predictive threat modelling. It constantly sifts through global threat intelligence feeds to identify emerging attack patterns and new techniques being used by cybercriminals. By understanding how attackers are likely to strike next, the endpoint solution can adjust its defences before an attack even begins.
This proactive stance dramatically cuts down the noise for human security teams. Instead of getting buried under thousands of low-level alerts (alert fatigue), they’re presented with a small number of high-priority incidents that AI has already investigated and contextualised. The result is a much faster and more accurate response.
The move toward this kind of intelligent security is accelerating. In Australia, the endpoint security market hit about USD 400 million in 2024 and is expected to more than double by 2033, a surge driven almost entirely by the integration of AI and ML. This growth makes it clear just how central AI has become to what endpoint protection is today.
How to Choose and Implement an Endpoint Solution

Alright, let's move from theory to action. Knowing what endpoint protection is and why it matters is one thing, but picking the right platform and getting it rolled out is where the real work begins. The market is flooded with vendors, each claiming to be the best, so making a smart choice requires a clear, structured game plan that fits your business like a glove.
A successful selection process always starts with a serious look in the mirror. Forget the flashy feature lists for a moment and focus on your actual risk profile. What are your most critical data assets? Who are your most vulnerable users? Answering these gut-check questions helps you zero in on what truly matters for your organisation.
Once you have that clarity, you can start weighing up potential solutions against a few key benchmarks.
Key Evaluation Criteria
When you're comparing endpoint protection platforms, you need to look past the marketing hype. Focus on these practical areas to see how they’ll actually perform in your day-to-day environment.
- Threat Detection Efficacy: How good is it at actually stopping threats? Don't just take the vendor's word for it. Look for independent test results from organisations like AV-Comparatives or the MITRE ATT&CK Evaluations. They provide unbiased, real-world data on how well a solution blocks genuine attacks.
- Management Console Usability: Your security team will be living inside this console every day. If the interface is clunky and confusing, it’s a recipe for missed alerts and human error. A clean, intuitive dashboard should be a top priority.
- Performance Impact: A security agent that grinds devices to a halt will kill productivity and frustrate your users into finding workarounds. Always test the solution's impact on system performance during a trial period—it’s a deal-breaker.
- Operating System Compatibility: This seems obvious, but it’s a common pitfall. Make sure the platform fully supports every operating system in your environment, from the newest releases to any legacy systems still kicking around. For a deeper dive on common business OS versions, check out our guide on the difference between Windows 11 Home and Pro.
A proof-of-concept (POC) is non-negotiable. Seriously. Choose your top two or three vendors and run a proper trial on a representative sample of your devices. This is the only way to truly validate a vendor's claims and see how the tool feels in your own environment.
Once you’ve made your choice, a smooth implementation is just as vital as the selection itself. Start by creating clear, enforceable security policies that define acceptable use and what to do when things go wrong.
Finally, invest time in training your people. A well-informed team is your first and most effective line of defence, transforming your endpoint protection from just another piece of software into a core part of your security culture.
Common Questions About Endpoint Protection
Jumping into the world of endpoint protection can definitely bring up a few questions. Let's tackle some of the most common ones I hear, with clear answers to help you get your head around the essentials and make smarter decisions for your organisation's security.
Is Traditional Antivirus Software Enough?
In a word? No. Traditional antivirus just isn’t enough anymore. It mostly relies on what’s called signature-based detection, which is a bit like having a security guard who only recognises known criminals from a photo book. The problem is, it can only spot threats that have already been identified and added to its list.
Cybercriminals are constantly churning out new zero-day exploits and fileless malware specifically designed to be unrecognisable and slip right past those outdated photo books. Modern Endpoint Protection Platforms (EPPs) have evolved, using next-generation antivirus (NGAV) that analyses behaviour to proactively block unknown threats. It's a much, much stronger defence.
What Is the Difference Between EPP and EDR?
This is a great question. Think of an EPP (Endpoint Protection Platform) as the shield and EDR (Endpoint Detection and Response) as the forensics kit. They have two very different but equally important jobs.
- EPP (The Shield): This is all about prevention. It uses tools like NGAV and firewalls to stop threats before they can get a foothold and cause any real damage.
- EDR (The Forensics Kit): This kicks in when something manages to sneak past the shield. It gives you deep visibility into everything happening on your endpoints, logs all the data for investigation, and hands your security team the tools they need to hunt down the threat and clean up the mess.
Most of the top-tier solutions today bundle both EPP and EDR into a single platform, giving you that complete coverage from prevention to response.
Will Endpoint Protection Slow Down Our Computers?
That’s a totally valid concern, especially if you remember the clunky, resource-hogging antivirus programs from back in the day. Thankfully, things have changed. Modern endpoint solutions are designed from the ground up to be lightweight and have a minimal impact on performance.
Many platforms now offload the heavy analytical work to the cloud. This means all the resource-intensive number-crunching doesn't happen on your local device, keeping your computers running smoothly while staying fully protected. The best way to be sure is to run a proof-of-concept to test the performance in your own environment.
Of course, for any software to perform well, the operating system underneath needs to be solid and up-to-date. You can learn more about securing your systems in our guide on the benefits of a genuine Windows 11 Pro license.
At Digital Hub Key, we provide authentic, affordable software keys to help you build a secure and efficient digital environment. Secure your systems today with genuine software from our online store.





