Australia
It’s a dangerous myth that small businesses are too small to attract the attention of cybercriminals. The truth is actually the complete opposite. Attackers often see smaller companies as easier targets precisely because they tend to have fewer security resources than big corporations.
Why Cybercriminals Target Small Businesses

Picture a thief walking through a massive car park. They aren't necessarily looking for the fanciest car; they're looking for the easiest one to break into. They'll just methodically check door after door, and the first unlocked one becomes their target.
Your small business is one of those cars. If your digital "doors" are unlocked—meaning you have weak passwords, outdated software, or no security training for your team—you become a target of opportunity. It's nothing personal; most of the time, it's completely automated.
The Myth of Being "Too Small to Notice"
Modern cyberattacks aren't usually carried out by a person sitting in a dark room picking out victims one by one. They’re often launched by automated bots that constantly scan the internet for known vulnerabilities. These bots don’t care if your business has two employees or two thousand. They are just programmed to find and exploit common weaknesses, like an unpatched operating system.
This is exactly why keeping your software up to date is so fundamental. Even understanding the security differences between Windows 11 Home and Pro can be a crucial part of your defence.
Because this approach is so widespread and automated, no business is ever truly "off the radar." In fact, because so many small businesses believe they are safe, they often neglect basic security hygiene, making them prime targets.
The Real-World Impact of a Breach
A single successful attack can have devastating consequences that ripple far beyond the initial financial loss. The fallout can disrupt your entire operation and completely destroy the trust you’ve worked so hard to build with your customers.
The potential damage includes:
- Financial Loss: This could be direct theft from your bank accounts, the cost of paying a ransom, or hefty regulatory fines for exposing customer data.
- Reputational Damage: Losing customer trust is incredibly difficult to win back. A data breach can permanently tarnish your brand's reputation.
- Operational Disruption: Downtime from locked systems or corrupted data can bring your business to a screeching halt for days or even weeks.
A common mistake is to only think about the immediate financial hit of an attack. It’s the long-term erosion of customer confidence and the sheer stress of recovery that can truly cripple a small business.
This threat is especially relevant here in Australia, where our preparedness is lagging behind the growing sophistication of cybercrime. A recent report found that while 83% of Australians believe cybercriminals are becoming more advanced, only a tiny 20% of small businesses have a dedicated cybersecurity policy in place.
You can dig deeper into these trends in the full Digital Lives of Australians report. Recognising this gap between threat and readiness is the first step toward building a truly resilient defence.
Understanding the Most Common Cyber Threats

To properly defend your business, you first need to understand what you're up against. Cyber threats can feel overwhelmingly technical, but at their core, they often rely on simple deception and predictable human behaviour. By learning to recognise the common tactics attackers use, you can turn your team into your most effective line of defence.
Think of it this way—you don't need to be a master locksmith to know you shouldn't hand your house keys to a stranger. In the same way, you don't need to be an IT genius to spot a suspicious email. It all starts with awareness.
Cyberattacks are a costly reality for Australian small businesses. In a recent 12-month period, 43% of small businesses reported experiencing at least one cyber attack. The financial fallout is just as stark, with the Australian Cyber Security Centre estimating the average cost per incident to be around $49,600. You can find more small business cybersecurity statistics on Heimdal Security to see the full picture.
To help you get started, here’s a breakdown of the most common threats your business is likely to face, explained with simple analogies and real-world examples.
Table: Common Cyber Threats and Their Real-World Impact
| Threat Type | How It Works (Simple Analogy) | Potential Business Impact |
|---|---|---|
| Phishing | A fake postal worker in a convincing uniform asks for your keys to "verify your identity." | Stolen login details for bank accounts, email, or critical software. |
| Ransomware | A burglar breaks in, locks all your filing cabinets, and demands cash for the key. | Complete operational shutdown, loss of all data, and significant financial demands. |
| Business Email Compromise (BEC) | A con artist perfectly impersonates your boss's voice on the phone to approve a fake payment. | Fraudulent fund transfers to criminal accounts, loss of thousands of dollars in a single transaction. |
Understanding these distinctions is the first step. Let's dig a little deeper into how each one plays out in the real world.
Phishing: The Art of Digital Deception
Phishing is one of the most widespread threats precisely because it targets people, not just technology. It’s a trick. An attacker sends an email that looks like it’s from a trusted source—your bank, a key supplier, or even a government agency.
These messages create a sense of urgency, pressuring you to click a link to update your details or download an "important" invoice. That link, however, leads to a fake website designed to harvest your login credentials. A classic example is an email claiming your Microsoft 365 account has been suspended, urging you to sign in immediately. The login page looks identical, but every keystroke is sent straight to the attacker.
Ransomware: Your Data Held Hostage
If phishing is a trick, ransomware is a digital kidnapping. It’s malicious software that, once inside your network, encrypts all your critical files—customer records, financial documents, project plans—making them completely inaccessible.
Imagine a criminal breaking into your office, locking every filing cabinet, and leaving a note demanding a hefty payment for the one and only key. That's exactly how ransomware works with your data. The attackers demand a ransom, usually in cryptocurrency, to provide the decryption key. But paying up is a huge gamble; there’s no guarantee you’ll ever get your data back.
Ransomware doesn't just lock your files; it locks up your entire business. For a small business, being unable to access invoices, customer lists, or daily schedules for even a few days can be financially crippling.
Business Email Compromise: The Impersonation Scam
Business Email Compromise (BEC) is a much more targeted and cunning attack. Think of it as sophisticated impersonation. An attacker might gain access to a manager's real email account or create a nearly identical one (e.g., jane.doe@yourcornpany.com instead of jane.doe@yourcompany.com).
They then use this trusted identity to send fraudulent instructions. The most common BEC scam involves the attacker, posing as the CEO, emailing the finance team with an urgent request to pay a new supplier or change bank details for a regular payment. Because the request appears to come from an authority figure, employees are often tricked into complying.
Keeping your systems stable and secure is a core part of resisting these attacks. For businesses looking for reliable performance, it might be worth learning about the benefits of Windows 11 LTSC for business environments in our detailed guide.
Building Your First Line of Digital Defence

Now that you have a clear picture of the threats, it's time to build your digital fortress. The good news? Foundational cybersecurity for small businesses doesn't need a huge budget or a dedicated IT department. It’s all about putting simple, high-impact measures in place that give you the biggest return on your effort.
Think of it like securing your physical storefront. You wouldn't rely on just one flimsy lock on the front door. You'd have a strong main lock, a deadbolt for extra security, and you'd make sure all the windows are properly sealed. Your digital security should follow the same layered approach.
Fortify Your Digital Doors with Strong Passwords
Passwords are the most common point of failure for many businesses. Weak, reused, or easily guessable passwords like "Admin123!" are the digital equivalent of leaving your key under the doormat. A cybercriminal doesn't need to be a genius hacker; they just need automated software that tries thousands of combinations in seconds.
The only way to counter this is with passwords that are long, random, and unique for every single account. But how can anyone possibly remember dozens of complex passwords? The answer is simple: you don't.
A password manager is an essential tool that acts as a secure digital vault for all your credentials. You only need to remember one strong master password, and the manager handles the rest, generating and storing uncrackable passwords for all your sites and services.
Add a Deadbolt with Multi-Factor Authentication
Even the strongest password can be stolen. That's where multi-factor authentication (MFA) comes in, and it's one of the single most effective security measures you can implement—often for free.
Think of MFA as the deadbolt on your door. Even if a thief manages to copy your main key (your password), they still can't get in without the second key (your phone or another device).
When you enable MFA, logging in requires two or more pieces of evidence to prove you are who you say you are:
- Something you know: Your password.
- Something you have: A one-time code sent to your phone or generated by an authenticator app.
This simple extra step blocks the vast majority of automated attacks. You should enable MFA on every critical account immediately, especially email, banking, and cloud storage platforms.
Patch the Cracks with Regular Software Updates
Outdated software is like having a broken window in your shop. It’s a well-known vulnerability that criminals actively look for and exploit. Developers are constantly releasing updates, not just for new features, but to patch security holes that have been discovered.
Ignoring these updates leaves your systems exposed. Many devastating cyberattacks, including ransomware infections, succeed by exploiting known flaws in software that a business simply failed to update.
Set your software and operating systems to update automatically wherever possible. This simple setting works around the clock to ensure your "digital windows" are always sealed, closing off easy entry points for attackers.
Automating this process removes the risk of human error or forgetfulness, ensuring your defences are always current. It's proactive maintenance and a cornerstone of effective cybersecurity.
Secure Your Devices and Network
Your team's computers, laptops, and mobile phones are all potential entry points into your business network. These devices, often called endpoints, are a primary target for malware, so implementing a solid defence here is crucial. We offer a deeper explanation in our guide on what is endpoint protection and how it creates a vital security layer.
Beyond individual devices, your entire network needs protection. This means securing your Wi-Fi with a strong password and ensuring your router's firewall is active. For a complete look at protecting these digital pathways, this essential guide to network security for small businesses offers practical steps your business can take today.
By layering these foundational defences—strong passwords, MFA as a non-negotiable second step, and consistent software updates—you build a resilient security posture. These actions transform your business from an easy target into a well-defended operation, ready to repel the most common digital threats.
Creating a Simple Team Security Policy
Your tech tools are important, but your strongest line of defence will always be your team. The problem is, you can't expect your staff to be mind-readers. They need clear, simple guidance on how to handle digital risks. This is where a security policy comes in—not as some dense legal document, but as a practical, one-page guide that empowers everyone to protect the business.
A good policy isn't about reciting abstract security goals. It’s about translating them into concrete, daily actions. Instead of overwhelming your team with jargon, the goal is to create a straightforward checklist covering the essentials of cybersecurity for small businesses. Think of this document as the foundation for building a security-conscious culture.
When your team understands the "why" behind the rules, they shift from passively following instructions to actively participating in the company's defence. They become a proactive ‘human firewall,’ spotting and stopping threats before they cause any real damage.
The Core Components of Your Policy
Your security policy doesn’t need to be a novel covering every possible scenario. Just start with the three areas where small actions make the biggest difference: passwords, email, and data handling. These pillars address the most common ways cybercriminals hit small businesses.
This infographic breaks down the simple, three-step process for structuring your policy.
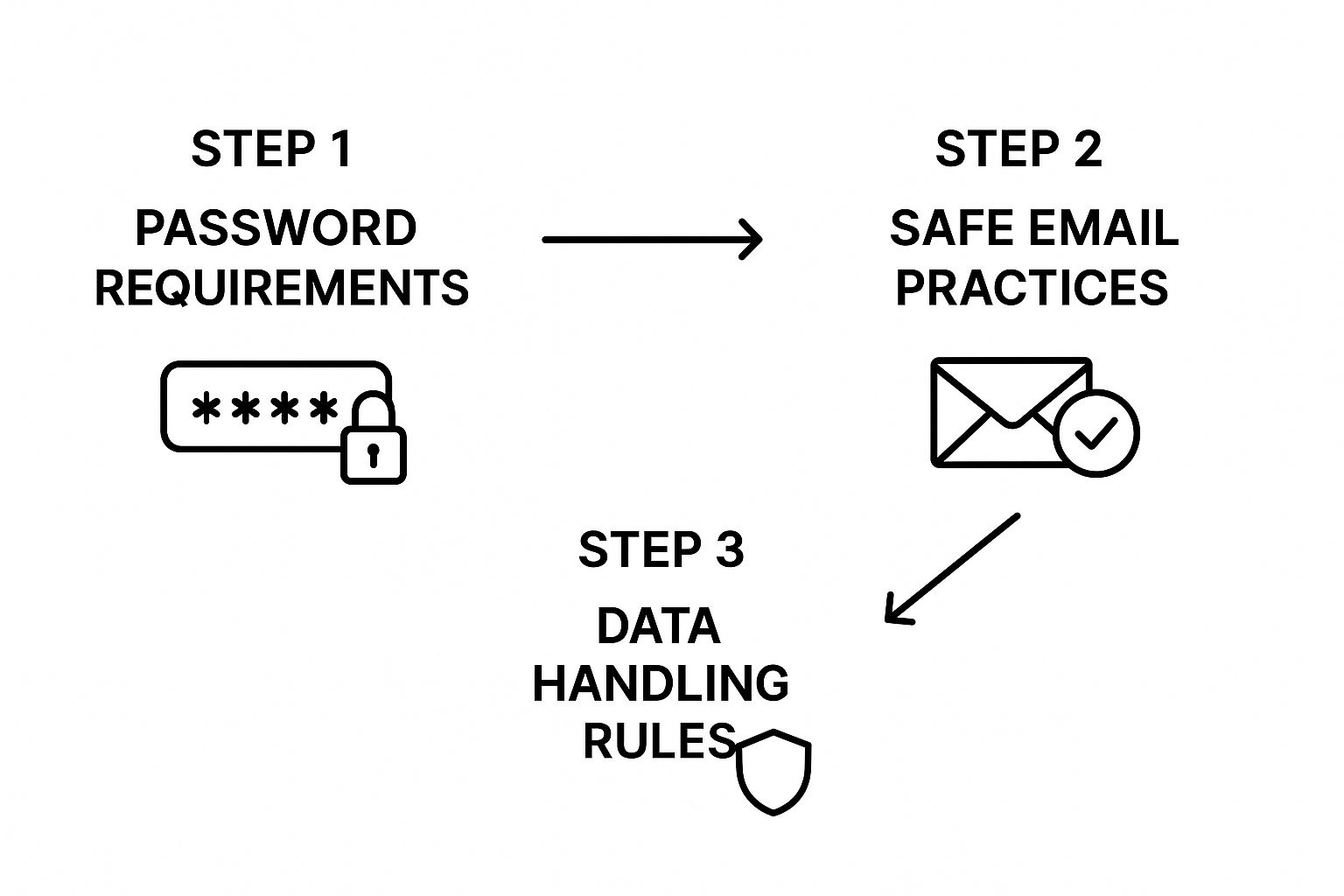
As you can see, it's a logical flow. Foundational rules for passwords lead to safer email habits, which in turn protect how your team handles sensitive data.
Breaking your policy into these manageable sections makes it easy for everyone to get on board. Let's dig into what each component should include.
1. Password and Access Requirements
Strong passwords are your first line of defence, but just asking for them isn't enough. Your policy needs to clearly state the minimum requirements for all company accounts, leaving no room for guesswork.
- Mandate a Password Manager: Require everyone to use a company-approved password manager. This simple step eliminates weak, reused passwords and the dreaded sticky note problem.
- Enforce Complexity Rules: Set a minimum password length of at least 12 characters and require a mix of uppercase and lowercase letters, numbers, and symbols.
- Require Multi-Factor Authentication (MFA): This is non-negotiable. Make MFA mandatory for all critical systems, including email, financial software, and cloud storage. Understanding what two-factor authentication is and why it’s so powerful is a crucial part of team training.
2. Safe Email and Internet Practices
Email is the number one way attackers get in the door. Your policy must provide clear do's and don'ts for handling emails and browsing the web.
A simple rule can prevent a major disaster: "When in doubt, don't click." Encourage your team to pause and verify any unexpected or urgent request, especially those involving payments or login credentials.
Your guidelines should instruct employees to:
- Never click links or download attachments from unknown or suspicious senders.
- Verify any requests for sensitive information or fund transfers through another channel (like a quick phone call).
- Avoid using public Wi-Fi for work without a company-approved VPN.
3. Handling Sensitive Data
You need to define what counts as "sensitive data"—customer information, financial records, employee details—and then establish crystal-clear rules for how it's handled.
This part of the policy should specify exactly where sensitive files are stored, who is authorised to access them, and how they can be shared securely. For example, you should explicitly forbid sending customer lists or financial spreadsheets via unencrypted email. Instead, direct your team to use a secure, access-controlled cloud platform. This simple step drastically reduces the risk of accidental data leaks and ensures your most valuable information stays locked down.
Preparing Your Data Breach Response Plan
When a cyber incident hits, panic is your worst enemy. Waiting for a crisis to decide what to do is a guaranteed recipe for disaster, turning a manageable problem into a catastrophic failure. An effective data breach response plan is like having a fire escape plan for your office; you hope you never need it, but it’s absolutely essential to have one ready to go.
Having a clear, pre-defined plan allows you to respond calmly and decisively, dramatically minimising the financial and reputational fallout of an attack. It’s a core part of a strong cybersecurity for small businesses strategy.
Unfortunately, many Australian small businesses are caught completely off guard. Recent data shows a staggering 74% of small businesses don’t have a data breach response plan. This is especially alarming when you realise that 47% of reported breaches involve small businesses, proving they are very frequent targets.
Why a Plan Is Non-Negotiable
A response plan isn't just some dry technical document; it's a business continuity tool. It gives you a step-by-step guide that removes all the guesswork during a high-stress event, ensuring you take the right actions at the right time.
This structured approach helps you contain the threat faster, figure out the extent of the damage, and communicate clearly with everyone who needs to know. A solid plan must also cover the potential legal consequences and defence strategies against cybercrime that can follow an incident. It’s about transforming chaos into a controlled, methodical process.
Your plan doesn't need to be overly complex. In fact, a simple, actionable checklist is far more useful than a hundred-page document that nobody ever reads. The goal here is clarity and speed.
Four Core Steps of a Small Business Incident Response Plan
When a breach occurs, every minute counts. Having a clear, four-step plan ensures you cover all your bases methodically, moving from immediate containment to long-term recovery without missing a beat. The table below breaks down these critical phases.
| Phase | Key Actions | Why It's Important |
|---|---|---|
| 1. Containment | Isolate affected systems from the network. Change all compromised passwords immediately. Preserve evidence for investigation. | This stops the breach from spreading further into your network and prevents more data loss—like closing the gate after an intruder gets in. |
| 2. Assessment | Identify what data was accessed or stolen. Determine the scope and severity of the breach. Engage cybersecurity professionals if needed. | You can't fix a problem until you understand its full extent. This phase informs your notification and recovery strategies. |
| 3. Notification | Contact your legal advisor and insurance provider. Inform affected customers and employees clearly and honestly. Report the breach to relevant authorities. | Transparency is crucial for maintaining trust. Prompt notification may also be a legal requirement under schemes like the Notifiable Data Breaches (NDB) scheme in Australia. |
| 4. Recovery | Eradicate the threat from your systems. Restore data from secure backups. Review the incident and update your security measures. | This phase is about getting your business back to normal operations and, crucially, learning from the incident to stop it from happening again. |
Following these steps in order helps turn a panicked scramble into a measured response, giving your business the best possible chance of a swift and successful recovery.
Building Your Response Team and Toolkit
Even a one-person business can have a "response team." This simply means identifying the key people and resources you will lean on in a crisis before it happens.
Your essential contact list should include:
- Your IT support or cybersecurity consultant: The first call you make for technical help.
- Your legal advisor: To guide you on your notification obligations and potential liabilities.
- Your cyber insurance provider: To understand your coverage and their required process for making a claim.
- Key business stakeholders: Such as your business partners or senior employees who need to be kept in the loop.
A crisis is the worst time to be searching for a phone number or trying to figure out who to call first. Prepare a simple contact sheet with names, roles, and contact details, and keep both a digital and physical copy accessible.
This proactive preparation ensures that when an incident occurs, you're not wasting precious minutes figuring out the basics. You can immediately move into action, following your plan and engaging the right support to navigate the crisis effectively. This readiness is what separates a minor disruption from a business-ending event.
Frequently Asked Questions
Jumping into cybersecurity can feel like learning a new language, and it's natural to have questions. Here are some straightforward answers to the queries we hear most often, designed to help you get started with confidence.
Let's cut through the noise and get to what really matters for your business.
How Much Should My Small Business Spend on Cybersecurity?
This is a classic "how long is a piece of string?" question. Costs can range from free, foundational tools all the way up to comprehensive managed services. The best approach is to start with high-impact, low-cost measures that give you the most bang for your buck.
Focus on these essentials first:
- Switch on multi-factor authentication for every critical account. It's usually free.
- Get a reliable password manager. Many offer affordable business plans.
- Invest your time in training your team to recognise obvious threats like phishing scams.
Remember, the cost of prevention is a tiny fraction of what it costs to clean up after a breach.
A small, consistent investment in the right tools and training now can save you a fortune—and your reputation—later. The average cybercrime incident costs an Australian small business around $49,600.
Where Is the Best Place to Start If I Feel Overwhelmed?
When you’re staring at a huge to-do list, it’s easy to feel paralysed. The trick is to start small and focus on what matters most.
Begin with your "digital crown jewels"—the data and accounts that your business absolutely cannot function without. This is usually your main business email, online banking logins, and primary cloud storage.
Pour all your initial energy into locking these down. The single most powerful action you can take is to enable multi-factor authentication (MFA) on all of them. Do it today. This one step creates a massive barrier against attackers trying to get in. For businesses running on Windows, exploring the security features that come with a Windows 11 Pro license is another smart move to harden your defences from the ground up.
Do I Really Need a Formal Response Plan?
Yes, you absolutely do. But don't let the word "formal" scare you. A simple, one-page checklist is infinitely better than having no plan at all when a crisis hits.
Having a plan removes the panic and guesswork from a highly stressful situation. It ensures you take the right steps, in the right order, to contain the damage and get back on your feet.
It also helps you meet any legal notification requirements here in Australia if customer data is involved. Think of it less as a stuffy corporate document and more as a practical emergency guide that leads your business back to safety.
At Digital Hub Key, we provide genuine, affordable software licences to help secure your business infrastructure. From operating systems to antivirus suites, get the tools you need with instant digital delivery. Secure your business today by visiting https://digitalhubkey.com.






[…] overwhelming, but it all starts with getting the fundamentals right. You can explore our guide on cybersecurity for small businesses to learn about essential protective measures tailored to your […]
[…] reputation. Getting a handle on the essentials is key, and guides explaining the fundamentals of cybersecurity for small businesses are an excellent place to […]
[…] is vital for protecting your firm's data. For a wider look at security basics, this guide on Cybersecurity for Small Businesses provides some great foundational […]
[…] one of the biggest wins of using managed services. Providers offer enterprise-grade solutions for cybersecurity for small businesses, giving them a resilient defence without the eye-watering […]
[…] of the best arguments for managed IT is the immediate security boost. A good MSP provides comprehensive cybersecurity solutions for small businesses from day one. They’ll build and manage a layered defence for you, which typically […]